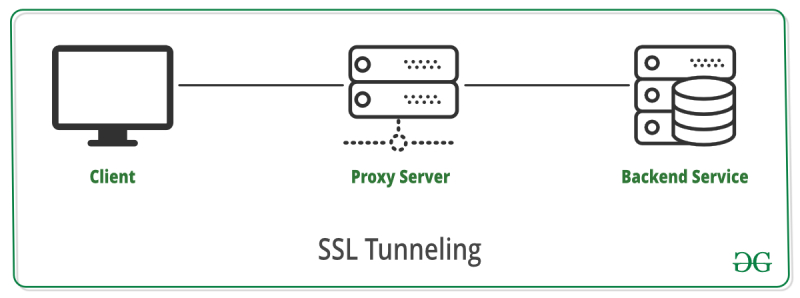
Utilizing the SSL Tunneling Approach
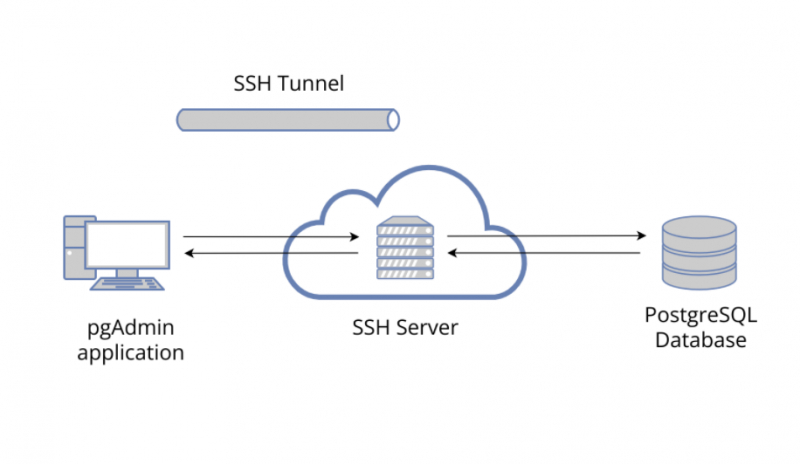
Another option is to employ SSL tunneling. This entails utilizing tunnel software to encrypt your OpenVPN-encrypted data yet again in order to conceal the fact that it's a VPN. The software for a tunnel is difficult to use, so while it is incredibly effective, it is also difficult to use if you aren't tech-savvy. SSH tunnels function similarly to tunnels, but your internet connection will be slower, and you'll need to learn a lot of code to set them up.
SSH (secure shell) is a cryptographic network protocol that permits safe authentication and data connections between two devices across open channels. SSH is essential for network and system administration (such as for managing firewalls, networks, servers, etc.). It's a client-server model system that tries to protect remote access between users and important systems over insecure connections, and it's physically integrated into Unix and Linux servers.