Top 10 Best Online Software Security Courses
Every software firm wants to ensure that its software security methods are the best in the industry. There is no question about that. However, in today's ... read more...complicated IT environment, with businesses utilizing more software than ever before and cyberattacks on the rise, ensuring software is genuinely safe can be difficult. These Best Online Software Security Courses can show you how to get the most bang for your buck. Buying the latest security product and calling it a day is never a viable security approach.
-
Everyone is affected by cybersecurity, including the supply of fundamental products and services. This is the course for you and your colleagues — from seasoned experts to non-technical colleagues — if you or your business want to better grasp how to address your cybersecurity. Are you interested in learning the fundamentals of cyber security? Are you an ambitious IT professional who wants to learn more about cybersecurity? If that's the case, this is the course for you!
In this 4-hour course, you'll walk through the foundations of cyber security, the core cyber security concepts you need to know and the numerous sorts of cyber threats. This course is essential if you want to progress or start a career in Information Technology (IT). After completing this course, you'll have a greater understanding of the fundamentals of cyber security, which will help you better safeguard your IT and business infrastructure! This course will provide the principles to understand the current debates shaping a rapidly evolving security landscape for students with some or no background in information technology.
Requirements:
- A Desire to Learn
- A Basic Understanding of Computers
Who this course is for:
- Non-Techies Wanting to Learn About Cyber Security
- Business & IT Managers Needing a Working Knowledge of Cyber Security
- Aspiring & Inexperienced IT Professionals
Course Rating: 4.9/5
Enroll here: https://www.udemy.com/course/cyber-security-for-absolute-beginners-essential-concepts/
https://www.udemy.com/ 
https://www.udemy.com/ -
One of the Best Online Software Security Courses is The Complete Cyber Security Course : Network Security! This course is about cyber security, privacy, and anonymity for personal and domestic use. The majority of the concepts are applicable to both businesses and individuals, however the course is taught as if it were to an individual for personal cyber security, privacy, and anonymity. Although it is not compulsory, it is advised that you watch volume 1 of this comprehensive course before proceeding to volume 2. The majority of the resources mentioned in this course are free.
However, you have the option of purchasing extra software, gear, or services that are addressed in the course. Although it is not required to purchase anything in order to comprehend and follow the course. You then shift your focus away from network security and onto the specifics of how businesses, nation-states, your ISP, and others monitor online. You'll learn about strategies like zombie super cookies, browser fingerprinting, and browser profiling, as well as how they function, so that third parties may figure out who you are online.
Requirements:
- You should be familiar with the fundamentals of networking
Who this course is for:
- Anyone who wants to become an expert in security, privacy, and anonymity
- Beginners and intermediate Internet users who are interested in security, safety, and privacy
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/network-security-course/
https://www.udemy.com/ 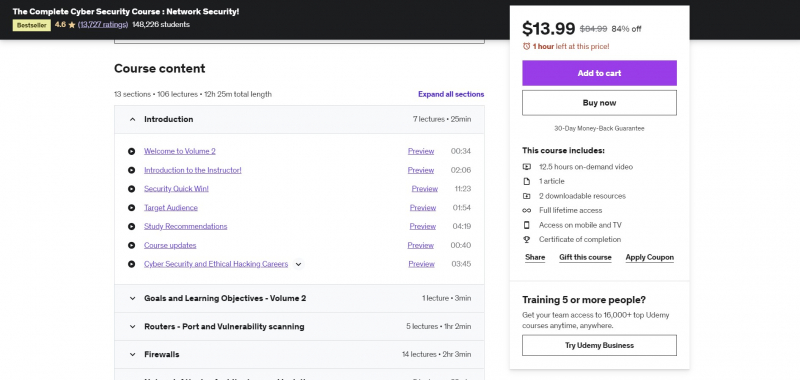
https://www.udemy.com/ -
Cyber Security: CISSP Certification is also one of the Best Online Software Security Courses. All in One This course on Udemy is for you: All-in-one CISSP Certification for Cyber Security. The field of cyber security is continually developing and improving as technology develops. One of the highest quality standards in the field of data security is the Certified Information Systems Security Professional certification. It is the gold standard in the business, and it is required for many mid- and senior-level roles. Organizations, in truth, have a lot more important things to accomplish than practice security. The CISSP (Certified Information Systems Security Professional) is a prestigious and internationally recognized certification.
The CISSP certification assists businesses in determining whether employees possess the skills, knowledge, and experience required to adopt sound security procedures. However, passing the final test is difficult. This Udemy course will guide you through the last weeks leading up to the CISSP test, providing you with a detailed schedule that covers all of the exam subjects. It will give you the courage to approach the test room knowing that you have done all possible to prepare for the big day. You will be confirmed as a skilled one after completing the CISSP exam, which is a PC based examination! So let's get this party started.
Requirements:
- Internet Access
- No pre-knowledge is required
Who this course is for:
- Anyone who is interested in Cyber Security
- Security Consultants/Managers
- IT Directors/Managers
- Security Auditors/Architects
- Security Systems Engineers
- Anyone who wants to pass the CISSP exam
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/cyber-security-cert-all-in-one/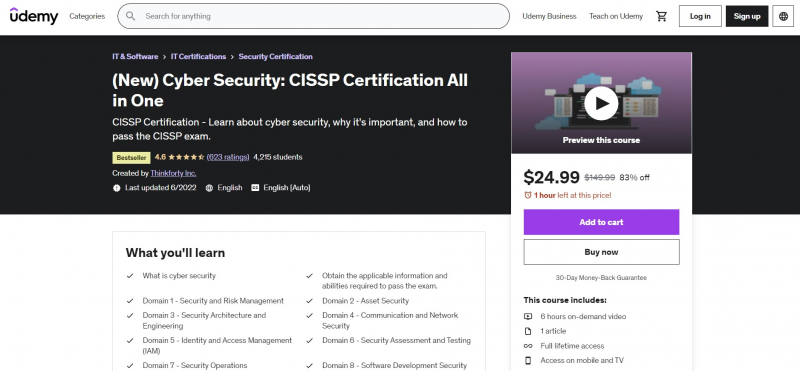
https://www.udemy.com/ 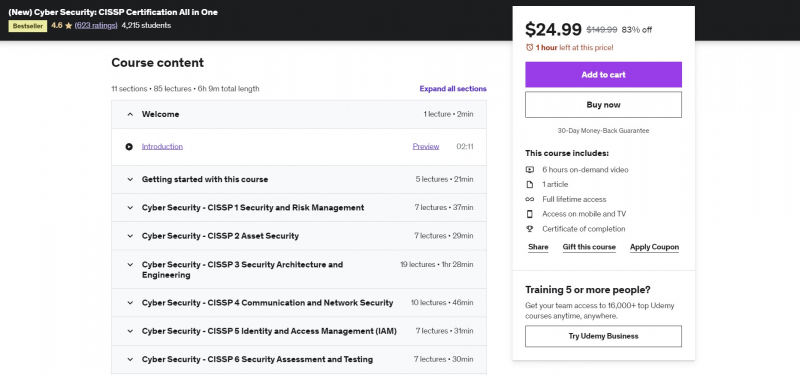
https://www.udemy.com/ -
Have you ever wondered how hackers actually 'hack'? Do you find terms like firewalls, encryption, biometrics, and malware to be perplexing? Have you been seeking for a course that will teach you all of the fundamentals of information and cyber security in a pleasant and casual environment? If that's the case, you'll find this course to be ideal for you. This is an excellent introduction course for adults and students interested in pursuing a career in cyber security or information security.
It is also appropriate for students who just wish to gain a broad understanding of the fundamental principles utilized in the field of information security. This course is designed for students who have little or no prior knowledge or experience in the subject of cyber security. You'll learn about the several types of malware, such as viruses, worms, and trojans, and how they vary. By the conclusion of this course, you will have obtained a wealth of information and insights that will assist you in launching your career as an information security specialist.
Requirements:
- You should know how to use a computer and internet
Who this course is for:
- Students who are interested in learning the fundamentals of computer and cyber security
- Students interested in pursuing a career in information technology or cyber security
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/the-absolute-beginners-guide-to-information-cyber-security/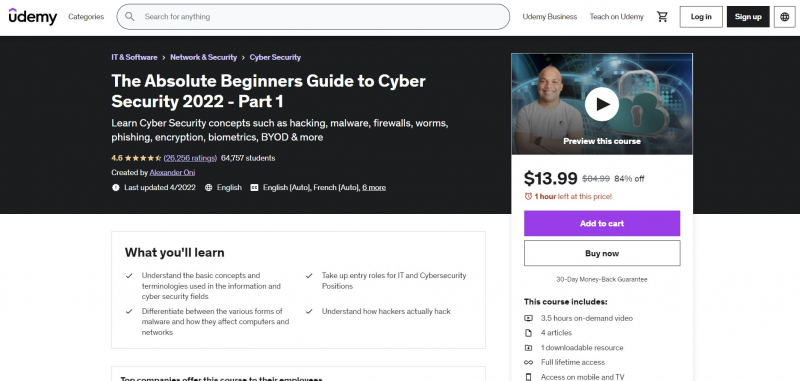
https://www.udemy.com/ 
https://www.udemy.com/ -
Welcome to Cybersecurity 2022: A Comprehensive Overview. This course will teach you the principles of information technology as well as the functioning components of cybersecurity. There are no prerequisites in terms of knowledge or expertise.
This course will give a springboard for you to master the essentials if you are a cybersecurity student, aspiring security professional, security enthusiast, or someone interested in learning more about the sector. As a current cybersecurity student, the teacher understands the types of worries, questions, and ideas you're having. He understood what concepts and abilities were lacking in the academic industry through focused effort, self-study, and industrial experience.
This course will provide a launchpad for you to acquire the core ideas, skills, and direction for you to get started in cybersecurity, whether you are a total newcomer to I.T. or the security side of I.T. You will learn the fundamentals of information technology from the ground up. The functional components of hardware, software, and operating systems, as well as computer networks, will be covered.
Requirements:
- No prerequisites
Who this course is for:
- Beginners
- Aspiring cybersecurity professionals
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/complete-introduction-to-cybersecurity/
https://www.udemy.com/ 
https://www.udemy.com/ -
A developer must study enough to become an architect over the course of several years. This learning is mostly determined by the options you have in your profession. Frequently, these chances are restricted to certain fields of labor. To be an architect, though, you must have a broad technical understanding of as many fields as feasible. You must be aware of all the complexity and difficulties that exist in various portions of a system.
You must be able to make informed judgments based on a thorough comprehension of potential trade-offs. You should be able to predict or foresee important issues that a system may confront as it evolves. The 'Developer To Architect' course will come in handy in this situation. It starts with the assumption that you already have excellent development abilities and grows from there. It goes through how to construct a system's non-functional qualities, how to handle large-scale deployments, and how to use popular open-source technologies to develop software solutions.
Requirements:
- You can design and create code in at least one programming language, and you are or have been a strong programmer
- You have a basic understanding of three-tier architecture and what web applications, services, and databases are
Who this course is for:
- All Software Developers and Architects
Course Rating: 4.5/5
Enroll here: https://www.udemy.com/course/developer-to-architect/
https://www.udemy.com/ 
https://www.udemy.com/ -
This course is among the Best Online Software Security Courses. It covers the essential building blocks of your necessary skill set: threat modeling and risk assessments will help you comprehend the threat and vulnerability landscape. After reading all four volumes, you'll know more about security, privacy, and anonymity than more than 80% of security experts, government and law enforcement personnel, and even experienced hackers. You'll learn about nation-state-run worldwide tracking and hacking infrastructures.
There's a whole crash course on encryption, including how it may be defeated and what you can do to limit the dangers. You'll learn about nation-state-run worldwide tracking and hacking infrastructures. The capabilities of the NSA, FBI, CIA, GCHQ, China's MSS, and other intelligence services are also covered in the course.
You'll be able to defend yourself against phishing, SMShing, vishing, identity theft, scams, cons, and other social engineering risks after completing the course. Finally, the course discusses isolation and compartmentalization, two critical yet underutilized security controls. Sandboxes, application isolation, virtual machines, Whonix, and Qubes OS are all discussed.
Requirements:
- A fundamental grasp of operating systems, networks, and the Internet is required
Who this course is for:
- Beginners and intermediate Internet users
- This course is about Internet security, privacy, and anonymity for personal and domestic use
Course Rating: 4.5/5
Enroll here: https://www.udemy.com/course/the-complete-internet-security-privacy-course-volume-1/
https://www.udemy.com/ 
https://www.udemy.com/ -
Cyber security is undeniably one of the most in-demand areas of IT right now, and will continue to be so in the future. And, because cloud technologies are such an important element of today's IT infrastructure and solutions, it's only natural that a substantial portion of cyber security research should be focused on the cloud. This course is designed to help you pass the CCSK certification test.
To do so, you'll obtain a thorough grasp of cloud computing's complete possibilities. You'll learn how to create a comprehensive cloud security program that adheres to internationally recognized standards. Finally, you'll learn how to use best practices in IAM, cloud incident response, application security, and other areas. Hands-on exercises, plenty of practice questions, and step-by-step advice for passing the CCSK test are all included in this CCSK course. This certification is regarded as a useful initial step for students interested in pursuing careers in IT and security.
Requirements:
- It is suggested that you have CompTIA A+ or comparable expertise
Who this course is for:
- Information Technology enthusiasts interested in learning the fundamentals of current cloud security
Course Rating: 4.4/5
Enroll here: https://www.udemy.com/course/complete-ccskv4/
https://www.udemy.com/course/complete-ccskv4/ 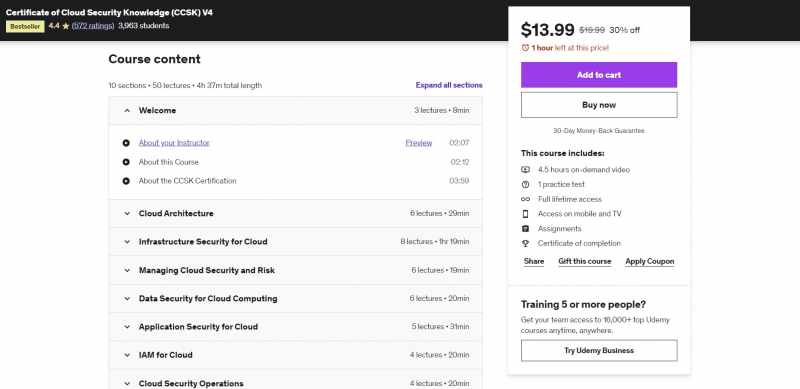
https://www.udemy.com/course/complete-ccskv4/ -
These days, one of the most significant parts of software architecture is software security. Almost every day, you read about new security breaches that resulted in data leaks, service disruptions, and, in some cases, billions of dollars in losses, with some organizations even shutting down as a result. As a software architect, it is your job to ensure that your architecture is as safe as feasible.
You just cannot allow yourself to release an insecure system. It's totally unacceptable these days. You must now be well-versed in all security elements of software design in order to create safe architecture. And that is precisely the purpose of this training.
You'll study the nomenclature of software security in this course, including concepts like SQL Injection, MFA, MITM, and more. After finishing this course, you will have everything you need to create the most secure software architecture available. You'll be able to download the Secure Architecture Checklist at the end of the course, which is a detailed checklist that will walk you through the process of creating secure systems, providing step-by-step instruction for each stage.
Requirements:
- A basic understanding of development is essential.
- It is suggested, but not required, that you be familiar with software architecture ideas.
- There is no need for a security background!
Who this course is for:
- Software Architects
- Developers
Course Rating: 4.4/5
Enroll here: https://www.udemy.com/course/software-architecture-security-the-complete-guide/
https://www.udemy.com/ 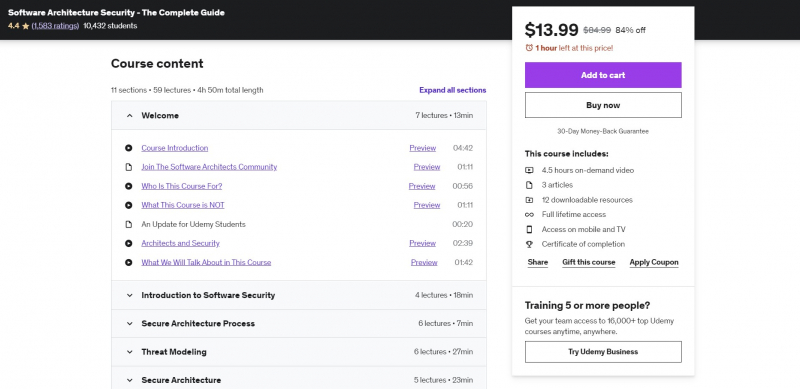
https://www.udemy.com/ -
This course will introduce you to the most prevalent vulnerabilities found in produced code, as described in publications such as the OWASP Top 10 and SANS Top 25. You'll learn how to identify which development patterns contribute to vulnerabilities and how to prevent them when writing safe code. You'll learn how to run a threat model on development features to figure out what kinds of dangers can affect your code, where they originate from, and how to deal with them.
You will also explore and use analytic tools accessible to developers in order to assess their code and find vulnerabilities early in the development life cycle, allowing you to repair them. Finally, you'll see how application security fits into a larger cyber security strategy.
This course gives a comprehensive review of all areas of application security. Even if you're not new to this area, it's a good idea to brush up on the concepts you're unfamiliar with, such as CSP, ASVS, Federation, Threat modeling, and OpenID. The explanation is straightforward, and each time, actual examples are provided.
Requirements:
- Web Application Knowledge is a plus
- Being a Developer
Who this course is for:
- Software Developer
- Web Developer
Course Rating: 4.3/5
Enroll here: https://www.udemy.com/course/application-security-the-complete-guide/
https://www.udemy.com/ 
https://www.udemy.com/