Top 6 Ways to Make Anonymous Crypto Payments
Although cryptocurrency offers a higher level of privacy compared to conventional currency, it doesn't always guarantee complete anonymity for its users. In ... read more...order to achieve complete anonymity, specific techniques or resources must be employed to ensure that one's identity remains fully hidden. Toplist has compiled a compilation of 5 Ways to Make Anonymous Crypto Payments.
-
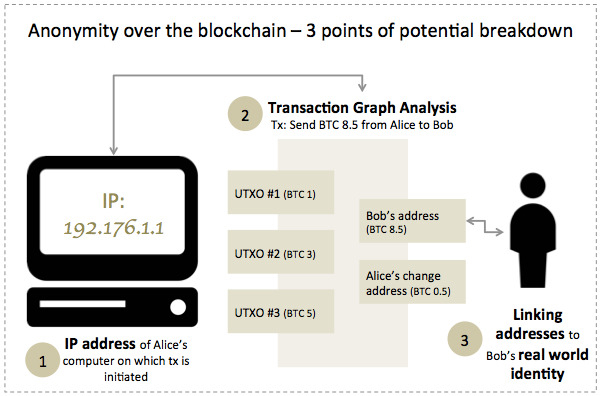
Stealth addresses employ cryptographic methods to augment the confidentiality and anonymity of cryptocurrency transactions, specifically those involving anonymous crypto transactions. These are one-time wallet addresses used in transactions instead of your real wallet address. These addresses are predominantly linked to privacy-centric cryptocurrencies such as Monero.
When you make a transaction using a stealth address, a one-time unique address is generated specifically for that transaction. This address is derived from the recipient's public key and additional random data. The sender uses this stealth address to transfer funds to the recipient.
The key feature of stealth addresses is that they prevent linkage between the sender's address and the recipient's address on the blockchain. When a transaction occurs, it is recorded on the blockchain, but the stealth address ensures that the recipient's actual address is not publicly visible. Instead, the recipient uses a private key to scan the blockchain and identify transactions addressed to them.
By utilizing stealth addresses, the privacy of both the sender and recipient is enhanced. Even if someone analyzes the blockchain, they cannot easily determine the recipient's actual address or link multiple transactions to the same recipient.
It's worth noting that stealthy addresses are just one component of a comprehensive privacy system. Privacy-focused cryptocurrencies like Monero employ additional techniques such as ring signatures, confidential transactions, and decoy outputs to provide a high level of privacy and anonymity for users.Pros:
- Enhanced privacy
- Improved anonymity
- Protection against address reuse
- User control over sharing addresses
Cons:
- Complexity and usability
- Reduced compatibility
- Potential privacy leakages
- Adoption challenges
Screenshot via https://coinloan.io/ 
Photo by Moose Photos via https://www.pexels.com/ -
Ring signatures, a distinctive attribute exclusive to Monero, distinguish it as the most popular privacy coin. The concept behind ring signatures revolves around creating a ring of potential signers. This ring typically consists of the actual signer and a group of decoys or mixins. Each participant in the ring generates a unique key pair: a public key and a private key. The actual signer uses their private key to create a signature, while the decoys utilize their private keys to generate additional signatures.
The magic happens when these signatures are combined. A sophisticated algorithm fuses the signatures into a single-ring signature that encapsulates the collective signing power of all participants. This amalgamation effectively disguises the true origin of the signature, preventing anyone from definitively linking it to a specific individual.
The verification process of a ring signature is equally remarkable. To verify the authenticity of a ring signature, anyone can utilize the public keys of the participants in the ring along with the ring signature itself. The process confirms the signature's validity without revealing the actual signer's identity.
The implications of ring signatures extend far beyond mere transactional privacy. They enable users to retain control over their personal information while engaging in financial activities. By obscuring the link between a transaction and an individual, ring signatures provide plausible deniability.Pros:
- Privacy Enhancement
- Anonymity
- Plausible Deniability
- User Control
Cons:
- Complexity
- Potential Vulnerabilities
- Computational Overhead
- Limited Adoption

Screenshot via https://www.makeuseof.com/ 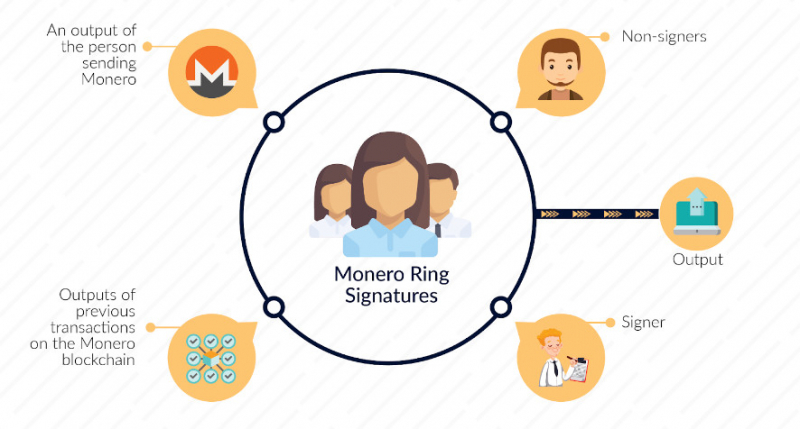
Screenshot via https://blog.pantherprotocol.io/ -
Virtual Private Networks (VPNs) are crucial in maintaining privacy and anonymity when making crypto payments. A VPN creates a secure, encrypted connection between your device and the internet by routing your internet traffic through an intermediary server. This server masks your IP address and encrypts your data, making it difficult for anyone to trace your online activities and link them to your identity.
When using a VPN for anonymous crypto payments, choosing a reliable VPN provider that values privacy is crucial. This ensures that even if someone requests your VPN provider's logs, there would be no data to link your transactions to your actual IP address.
You can further enhance your privacy by connecting to a VPN server in a different geographic location. This makes it harder for anyone monitoring the network to associate your transactions with your physical location. Additionally, some VPN providers offer features like multi-hop connections or onion routing, which provide an extra layer of anonymity by routing your connection through multiple servers.
While there are numerous free VPN options available, it is essential to be aware of the potential drawbacks that come with them. These drawbacks may include the logging of user data and subpar encryption methods. You should choose respected paid providers such as ExpressVPN and CyberGhost to ensure the highest quality VPN service.
Pros:
- Enhanced Privacy
- Anonymity
- Security
- Access to Restricted Content
Cons:
- Trust in VPN Provider
- Potential Speed Reduction
- Potential for False Sense of Security

Screenshot via https://www.makeuseof.com/ 
Screenshot via https://www.kaspersky.com/ -
Bitcoin ATMs, also known as BTMs or Bitcoin kiosks, are physical machines that enable users to buy or sell Bitcoin using cash or other forms of payment. These machines typically resemble traditional ATMs but are specifically designed for cryptocurrency transactions.
Bitcoin ATMs provide a convenient way for individuals to acquire or dispose of Bitcoin without a traditional exchange or online platform. They allow users to convert their fiat currency, such as cash, credit, or debit cards, into Bitcoin or vice versa.
To ensure anonymity when using a Bitcoin ATM, it's important to note that providing your Bitcoin address when prompted may compromise your transaction's complete anonymity. However, if you claim you don't have a Bitcoin address, the ATM will generate a paper wallet address. This address can be used multiple times, but for optimal anonymity, it's recommended for one-time transactions only. By doing so, the address cannot be linked back to you, ensuring your crypto activities remain untraceable.
Pros:
- Anonymity
- Convenience
- Additional layer of security
Cons:
- Limited Availability
- Transaction Fees
- Regulatory Compliance
- Lack of Regulation

Photo by Worldspectrum via https://www.pexels.com/ 
Screenshot via https://www.fiahub.com/ -
A Bitcoin mixer, called a Bitcoin tumbler, conceals the link between a transaction and the wallet addresses involved. It aims to mix the funds from your transaction with other users' transactions. During the process, these funds are combined in a pool and mixed. As a result, it becomes impossible to determine which user sent which batch of coins when they exit the mixer.
Furthermore, the mixer software is the recipient address for individuals receiving Bitcoin funds. This additional measure safeguards the recipient's identity from being traced. Consequently, both the origin and destination of the Bitcoin become untraceable.
Bitcoin mixers exist in two primary forms: centralized and decentralized. Centralized mixers are operated by dedicated companies, whereas decentralized mixers function on a peer-to-peer basis, without any single entity having control over the network. When using a centralized mixer, it is crucial to trust the tool's security measures and ensure that your address remains concealed. It is also advisable to conduct thorough research on the centralized mixer you are considering, ensuring it has positive reviews and is deemed safe.
Pros:
- Crypto exchanges
- Protection against Surveillance
- Decentralized Trust
Cons:
- Legality and Regulatory Concerns
- Trust in Mixer Providers
- Potential Loss of Funds
- Reduced Anonymity

Photo by David McBee via https://www.pexels.com/ 
Photo by Ivan Babydov via https://www.pexels.com/ -
KYC, or Know Your Customer, is a financial regulation that mandates individuals using financial services to verify their identity. To complete the KYC process, users must provide personal details such as their name, address, contact information, and a valid identification document like a passport or driver's license. It is virtually impossible to maintain anonymity on an exchange that implements KYC.
However, not all cryptocurrency exchanges enforce KYC requirements. If your goal is to remain completely anonymous, consider using an exchange that doesn't have KYC procedures in place. Examples of non-KYC exchanges include PrimeXBT, Bybit, CoinEx, and Bisq. On the other hand, all the biggest crypto exchanges, Binance, Coinbase, and Kraken, have mandatory KYC verification. If you decide to utilize a lesser-known exchange, it is crucial to conduct thorough research to ensure its safety and legitimacy.
For an even higher level of anonymity, you can opt for peer-to-peer-only exchanges that don't implement KYC. On these platforms, transactions occur directly between users rather than involving the exchange itself. When selecting a user to trade with, be mindful of their listed payment options and avoid individuals who require your personal information, such as your name and email address.
Pros:
- Compliance with regulations
- Enhanced security
- Customer protection
- Trust and credibility
Cons:
- Privacy concerns
- Accessibility limitations
- Time-consuming process
- Exclusion of unbanked individuals

Screenshot via https://www.makeuseof.com/ 
Screenshot via https://coin98.net/