Top 10 Best Online Cryptography Courses
People have utilized cryptography to keep things safe since Julius Caesar's rule in 100 BC, and owing to online learning, you can do it on your own. ... read more...Cryptography is becoming an important part of digital security, and many people are enrolling in online cryptography courses to learn these valuable skills. Let's explore the Best Online Cryptography Courses to access useful knowledge and how to apply it in your life and work.
-
Cryptography is a crucial technology for safeguarding data in computer systems. Cryptography 1 is one of the Best Online Cryptography Courses. This course will teach you how cryptographic systems operate and how to utilize them appropriately in real-world applications. The course starts with a comprehensive explanation of how two people with a shared secret key may communicate securely even if a formidable opponent listens in and tampers with communications.
The course focuses on a variety of protocols in use and look for flaws in existing systems. The course's second half covers public-key approaches, which allow two people to construct a shared secret key. Participants will be introduced to a variety of intriguing open topics in the area and will work on enjoyable (optional) programming projects during the course. The course will cover more complex cryptographic tasks such as zero-knowledge, privacy methods, and other types of encryption in a second course (Crypto II).
Look for classes that allow you to practice encryptions and other types of cryptography while you're taking them. This not only helps you remember the content better, but it also allows you to graduate from the course with a solid foundation of knowledge.
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
- Approx. 23 hours to complete
- Subtitles: English
Course Rating: 4.8/5
Enroll here: https://www.coursera.org/learn/crypto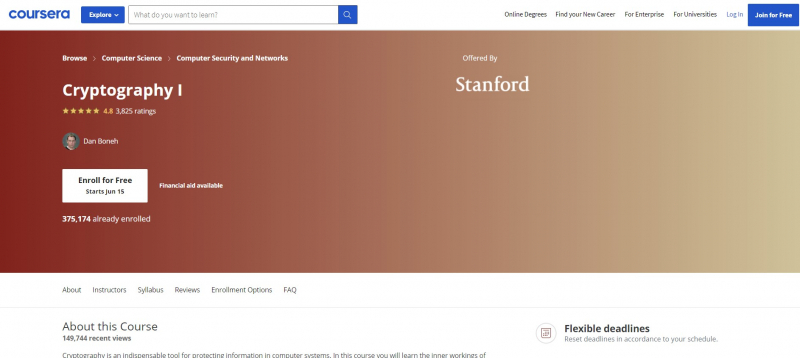
https://www.coursera.org/ 
https://www.coursera.org/ -
Cryptography: A Hands-on Approach is among the Best Online Cryptography Courses. In cybersecurity, cryptography is essential. It serves as the foundation for numerous defense methods, systems, and protocols. You won't be able to do many activities on the Internet safely without cryptography, such as web browsing, online banking, working remotely, and so on. Blockchain and cryptocurrency will not exist without crypto.
You will go through the fundamentals of cryptography in detail in this course. The course concentrates on secret-key encryption, one-way hash functions, and public-key cryptography, which are the three fundamental pillars of cryptography. It looks at how they function and how they're applied in real-world scenarios.
The course also considers the dangers individuals encounter and how these dangers are dealt with in the actual world. It also looks at some of the most typical blunders individuals make while utilizing encryption algorithms and protocols. The course demonstrates how these flaws can be used against you in an attack. Hands-on learning is emphasized throughout the course.This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
- Approx. 11 hours to complete
- Subtitles: English
Course Rating: 4.8/5
Enroll here: https://www.udemy.com/course/du-cryptography/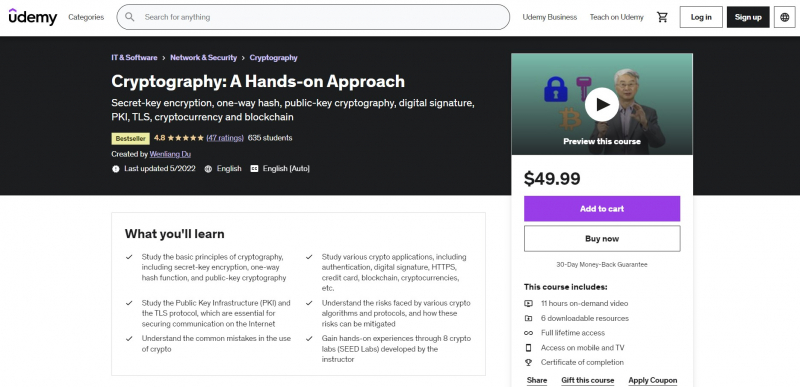
https://www.udemy.com/ 
https://www.udemy.com/ -
The science of secrets and hidden transmissions is known as cryptography. The Mathematics of Cryptography with Dr James Grime is also one of the Best Online Cryptography Courses. The course will begin with simple ciphers and how they were cracked before progressing to more complex ciphers such as the famed World War II Enigma machine and current internet encryption. There are more than 6 hours of lectures in this course, plus 2 hours of exercises and solution videos.
Many key mathematical ideas will be introduced in this course, including modular arithmetic, sets, functions, probability, statistics, combinatorics, and number theory. Finally, you will take a look at the future of cryptography to round up the course. After each session, there are several activities with solutions that allow you to put what you've learned to the test. Cryptography is one of the most exciting applications of mathematics, covering a wide range of issues. By the end of this brief course, it has covered some important concepts in mathematics and even addressed the question of whether an unbreakable code exists.
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
- Approx. 8 hours to complete
- Subtitles: English
Course Rating: 4.7/5
Enroll here: https://www.udemy.com/course/the-mathematics-of-cryptography-with-dr-james-grime/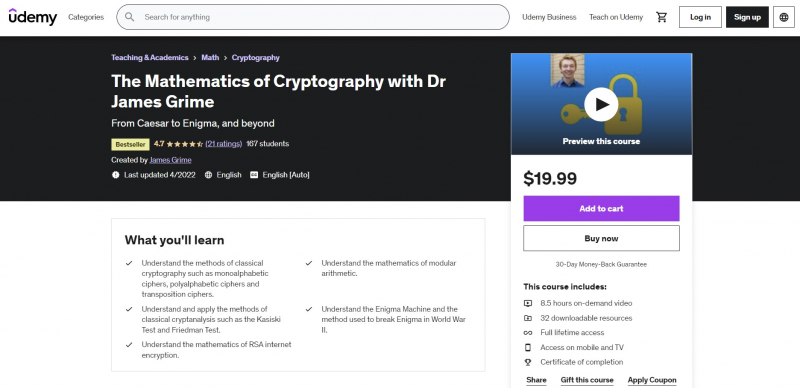
https://www.udemy.com/ 
https://www.udemy.com/ -
The main and important ideas for functioning as an IAM Expert are covered in this course. Identity and Access Management (IAM) is the process through which a company secures resource access for its workers and the general public. To establish a secure IAM for an enterprise, it is a mix of diverse technologies, policies, and ongoing tweaking, rather than a single solution or product.
This course starts with the fundamentals of Microsoft Active Directory, and then moves on to how to set up Active Directory for a small business. This section's labs are all demonstrated in Azure, so you get more here. You will study Microsoft AD CS in the second half of the course. AD CS is a Microsoft internal PKI solution that includes everything you need to set up a Certificate service. You'll start with the fundamentals of cryptography, then move on to ADCS and eventually to implementing all of Microsoft AD CS's functionality, including a SMART CARD login.
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
- Approx. 5 hours to complete
- Subtitles: English
Course Rating: 4.7/5
Enroll here: https://www.udemy.com/course/iam-pki-adfs-azuread-saml-mfa-openid/
https://www.udemy.com/ 
https://www.udemy.com/ -
You'll learn about cryptography and hashing in Python and Java in this course. The majority of the private key (symmetric) and public-key (asymmetric) cryptosystems will be explained step by step. Every cryptographic algorithm's theory and implementation may be learned, as well as how to crack these systems (so what are the weaknesses).
An IT security specialist can provide you with useful security background knowledge. Learn how to stream-based and in-memory encode hashes. Learn how to appropriately utilize salt and iteration count for safe password hashing using the PBKDF2 algorithm from the PKCS#5 security standard. Today, this is one of the most widely used secure hashing protocols.
To take this course, you must be a seasoned Java developer. There are some hands-on coding exercises that you can utilize right away in your own (business) applications! Although there are utilizing an earlier version of Eclipse in this course, the information is still current. This is due to the fact that PBKDF2 may be employed with today's processing power by simply raising the 'famous' iteration count (as used in various applications like VeraCrypt).
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Intermediate Level
- Approx. 13 hours to complete
- Subtitles: English
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/learn-cryptography-basics-in-python/
https://www.udemy.com/ 
https://www.udemy.com/ -
Yes, you read that correctly. This zero to hero series may turn you become a Super Hacker from Script Kiddie. Unlike other Ethical Hacking courses, this one focuses on the computer principles and essentials needed to become an excellent evergreen hacker. Other hacking classes will teach you the necessary tools and methods. As the system matures, these tools become outdated. As a result, you become a script kiddie rather than a hacker.
The course starts with Information Security Policy and Principles, then moves on to teaching you computer language (Binary), and eventually brings everything together to comprehend Cryptography, Crypt-analysis, and Digital Signatures. System and Network Security (Part -3) of the curriculum covers Applied Cryptography subjects such as SSL, NTLM Hash, Noedham-Schroder Protocol, Kerberos, and others. However, you must be extremely clear with Part 3 in order to grasp it. This course is designed for those who want to become excellent Ethical Hackers but don't have the requisite computer foundations, enthusiasts, or persons who work in law enforcement agencies.
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
- Approx. 2 hours to complete
- Subtitles: English
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/ethical-hacking-basics-part-1-cryptography/
https://www.udemy.com/ 
https://www.udemy.com/ -
For obvious reasons, security and Cryptography are a need in today's internet applications. To begin, you must safeguard data that you do not want others to have access to; otherwise, the internet is open by default, and anybody may eavesdrop on your personal information; and you must defend yourself from basic breaches. You must have a basic grasp of the underlying security concepts if you want to feel comfortable with Cryptography and security. Understanding the most common blunders can help you build cryptographic algorithms correctly.
The course will cover all cryptographic ideas and security concepts in this course so that you can comprehend the whole TLS/SSL protocol stack, password validation, and more. You'll be learning as you go, implementing encryption and authentication methods and making mistakes along the way to fully comprehend and understand the security vulnerabilities. The course comes with a 30-day money-back guarantee, so if you're not happy, you may get your money back.
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
- Approx. 7.5 hours to complete
- Subtitles: English
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/learn-modern-security-and-cryptography-by-coding-in-python/
https://www.udemy.com/ 
https://www.udemy.com/ -
Advanced Cryptography Concepts, a deep dive into the benefits, drawbacks, use cases, limits, and limitations of symmetric, asymmetric, Hashing, algorithms, Public Key Infrastructure, Certificate Authorities, Secure Channels, TLS, and standards. The good, bad, and ugly for all symmetric and asymmetric algorithms with practical use cases for how algorithms are used today and how their weaknesses are discovered and broken, such as with WEP and DES, are covered through explains of Applications of Cryptography, Private and public key pairs, and Binary math.
Cryptographic Secure Channels and cybersecurity defensive countermeasures, cryptanalysis assaults, cryptography standards such as VPS, IPSEC, AH, and ESP, and important cryptosystem attacks. This course covers all important symmetric and asymmetric algorithms, as well as the full encryption system, including the use of the CIA triad in cryptography and a discussion of how Blockchain works as a security solution. All videos come with course materials. The course is divided into five sections, each featuring over 13 symmetric algorithms.
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
- Approx. 4.5 hours to complete
- Subtitles: English
Course Rating: 4.4/5
Enroll here: https://www.udemy.com/course/advance-cryptography-concepts/
https://www.udemy.com/ 
https://www.udemy.com/ -
Are you preparing for a cryptography interview? Don't be concerned; instead, take this Cryptography quiz to prepare for your interview. It will develop your confidence by offering tips and tricks for solving Cryptography related questions with this Cryptography based Quiz. There will be a series of practice exams in this Cryptography Multiple Choice Questions Quiz where you may test your Basic Knowledge in Cryptography. Cryptography is a branch of mathematics and logic that is used to create secure encryption systems.
To cover the ocean of topics in cryptography, you'll need to consult a range of books and websites. To make things easier for you, it compiled a list of Cryptography-related questions from many disciplines. If you can answer these questions correctly, your confidence will skyrocket. The applicants take the Cryptography Based MCQ Test right away and grasp the numerous questions and answers. This course is for those who want to learn how to become professional ethical hackers.
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
Course Rating: 4.4/5
Enroll here: https://www.udemy.com/course/fundamentals-of-cryptography/
https://www.udemy.com/ 
https://www.udemy.com/ -
This course will teach you about all of the ancient and new security systems that have been employed and are still in use. You'll also discover how to break each one and why certain security measures are weak while others are robust. Let's go through the three primary current cryptography technologies in use today: RSA, AES, and ECC. Security is a crucial tool, and the capacity to hide information through mathematics is crucial to the world.
Take a look at how our banks and even the National Security Agency (NSA) protect their data. You may even apply for security employment at sites like the NSA if you know what you're doing with this course! The majority of today's security is built on RSA and AES, although the NSA is promoting Elliptic Curve Cryptography as a more secure alternative to RSA.
All of these cryptosystems, as well as their flaws, are covered in this course. This cipher has an example. Only a few individuals are aware of these methods at the moment, and you might be one of them. The most enjoyable aspect of this training is deciphering the codes.
This course offers:
- Flexible deadlines: Reset deadlines in accordance to your schedule.
- Certificate: Earn a Certificate upon completion
- 100% online
- Beginner Level
- Approx. 30 mins to complete
- Subtitles: English
Course Rating: 4.0/5
Enroll here: https://www.udemy.com/course/cryptography-ethical-hacking-course/
https://www.udemy.com/ 
https://www.udemy.com/