Top 10 Best Online Cyberattacks Courses
Cybersecurity is becoming more of a concern for both organizations and individuals, and there is a growing need for cybersecurity training. Would you wish to ... read more...improve the security of your home or workplace? Perhaps you're an employer that wants to improve your company's security and educate your staff on the subject. Perhaps you're thinking in pursuing a career in cybersecurity and aren't sure where to begin. Beginners might benefit from the Best Online Cyberattacks Courses.
-
One of the Best Online Cyberattacks Courses is The Beginners 2022 Cyber Security Awareness Training Course. This course includes 40 brand new '1:M Cyber Security' training videos that cover over 29 different cyber security topics. The teacher will speak passionately and directly to you about the most serious cyber security dangers you face today. It's jam-packed with the newest social engineering techniques used by hackers and fraudsters to get your data, money, and secrets. You'll start by viewing a lot of VISUAL examples of targeted phishing emails and learning how to see the primary red flags so you can READILY detect similar emails in the future.
You'll see how search engines like Google are abused for malicious ends. Banking Trojans, a popular sort of cyber attack that effectively drains your bank accounts of cash, will be explained. You'll also learn about Fake Antivirus, a very powerful and successful means of socially engineering people into passing over credit card information. You'll learn why Apple machines are generally safe, but can be just as insecure as other computers at times, as well as some basic precautions you can take when using a Mac computer.
Requirements:
- Without any prior knowledge
Who this course is for:
- Employees in a business or corporation
- Someone who wants to browse the Internet securely and privately
- Beginners
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/1m-cyber-security-awareness/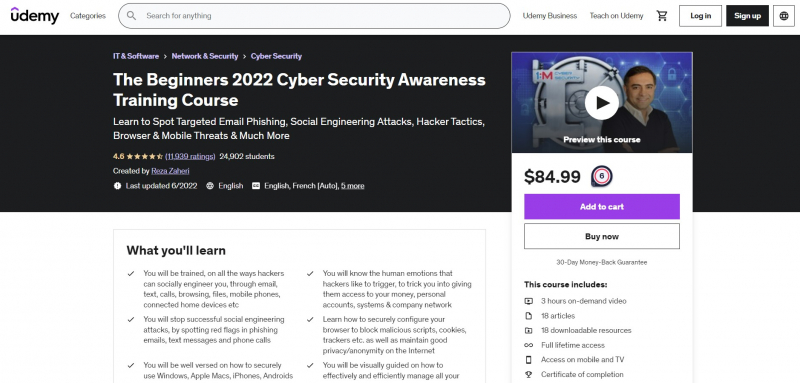
https://www.udemy.com/ 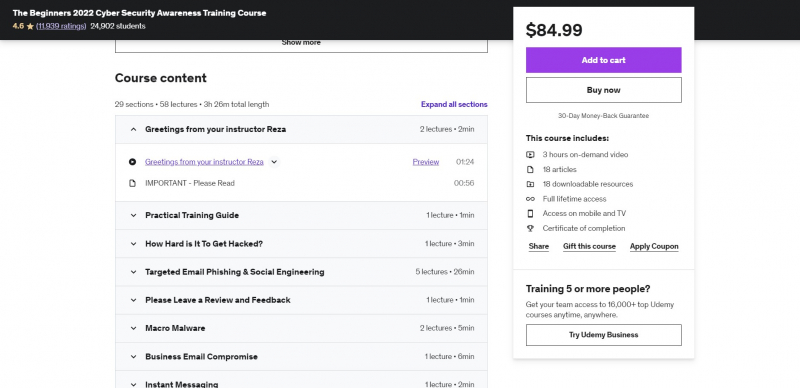
https://www.udemy.com/ -
Global expenditure on cyber security goods and services will top $1 trillion by 2021, according to a Forbes magazine article. Companies and governments throughout the world will continue to have a high need for cyber security specialists, according to experts. It's no surprise that many people are exploring a career in the burgeoning cyber security field. However, being a cyber security specialist is difficult and fraught with ambiguity.
This course is ideal for students planning to attend college or university to pursue a career in cyber security. It's also intended to assist current employees who want to make a career shift and are interested in pursuing a new career in cyber security. You'll learn about the many positions and occupations accessible in the cyber security field.
You'll learn about many sorts of certificates and how to choose which ones are appropriate for your professional path. Not only will you have a thorough awareness of the types of employment available in the field by the end of this course, but you will also be able to devise a strategy for becoming a successful cyber security specialist.
Requirements:
- Be able to use the internet
- Be interested in pursuing a career in cyber security
Who this course is for:
- Anyone
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/becoming-a-cyber-security-professional-the-complete-guide/
https://www.udemy.com/ 
https://www.udemy.com/ -
Have you ever questioned why the executives or management of your company decided to support or not fund your project? This course will give you an inside look at how cybersecurity and information technology (IT) executives decide which projects to fund and which to reject based on a preliminary risk assessment. The teacher spent the last two decades working in the field of cybersecurity and information technology, battling for funding for the teacher's initiatives. It all came down to risk management by the leaders and managers.
You'll learn how to apply risk management ideas to your networks, systems, and projects, as well as the phrases used by executives and managers when discussing risk management. This is not an operational or tactical training about how to protect your networks; instead, it focuses on managers' mindsets and teaches you how to think as they do. It will be much easier to develop your business case for your initiatives and explain your financial demands after you have mastered these ideas.
Requirements:
- No special tools are required
Who this course is for:
- Information Technology mangers
- Cybersecurity managers
- Aspiring managers
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/risk-management-for-cybersecurity/
https://www.udemy.com/ 
https://www.udemy.com/ -
Have you ever wondered how hackers actually 'hack'? Do you find terms like firewalls, encryption, biometrics, and malware to be perplexing? Have you been seeking for a course that will teach you all of the fundamentals of information and cyber security in a pleasant and casual environment? If that's the case, you'll find this course to be ideal for you.
This is an excellent introduction course for adults and students interested in pursuing a career in cyber security or information security. It is also appropriate for students who just wish to gain a broad understanding of the fundamental principles utilized in the field of information security.
This course is designed for students who have little or no prior knowledge or experience in the subject of cyber security. By the conclusion of this course, you will have obtained a wealth of information and insights that will assist you in launching your career as an information security specialist. So, what exactly are you waiting for??? Let's enroll in this best-selling course.
Requirements:
- You should know how to use a computer and the internet
Who this course is for:
- Students who are interested in learning the fundamentals of computer and cyber security
- Students interested in pursuing a career in information technology or cyber security
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/the-absolute-beginners-guide-to-information-cyber-security/
https://www.udemy.com/ 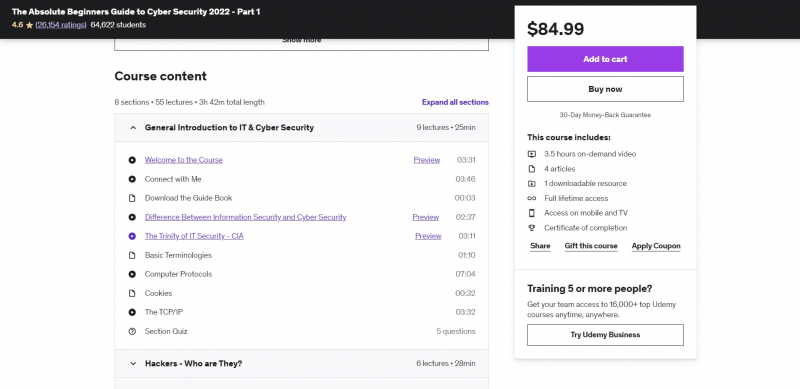
https://www.udemy.com/ -
A Complete Cyber Security Guide For Beginners 2022 is also one of the Best Online Cyberattacks Courses. You will learn all you need to know about cyber security in this course, including not just technical specifics but also career paths. This course includes all you need to know about cyber security, from the fundamentals to making money with it. Plus, the teacher will share his own experience with real-life SCAMMERS and how to outsmart them! In the sphere of cyber security, he will teach you how to EARN money in an ethical manner. Dhabaleshwar Das, the CEO and Founder of 7 Defence, teaches this training (Which is a leading company in the field of Information Security).
More than 100,000 cyber security specialists have been taught by him. His pupils have passed not just easy tests like CEH, but also some of the most difficult ones like CISM and SSCP. Vulnerabilities, Malwares, Encryption, WordPress Security, Google Dorks & Google Hacking Database, Digital Certificates, Social Engineering, Phishing, Scammers, Hacking, Earning money in the field of Cyber Security, and other subjects will be covered in this course.
Requirements:
- Nothing except a positive attitude
Who this course is for:
- Anyone
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/a-complete-cyber-security-guide-for-beginners/
https://www.udemy.com/ 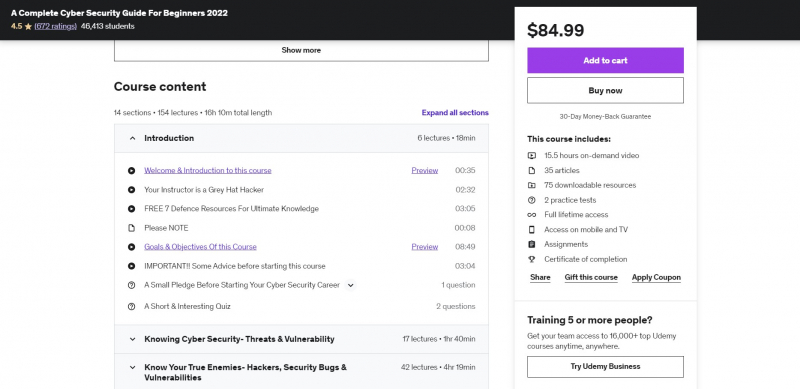
https://www.udemy.com/ -
Cyber Security: From Beginner to Expert (2022) is among the Best Online Cyberattacks Courses. A complete beginner level course that contains step-by-step explanations of essential security principles, as well as follow-up tests and hands-on laboratories, to ensure that the course taker has a strong understanding of the material. This course has been prepared by a Cyber Security specialist with a PhD degree and premium Cybersecurity certifications to make learning complicated Cyber Security subjects exceedingly simple. This course is designed for novice Cyber Security professionals and will assist you in mastering the important areas and launching a successful career in the sector.
It's also a wonderful place to start for students interested in CompTIA Security+ and CEH certifications in Cyber Security. Please watch free sample films to observe how difficult ideas are taught in a simple manner! The six hands-on laboratories will teach you skills that you may apply right away in the workplace: Practice cryptography by using the RSA technique to generate public-private keys, encrypting data with the public key and decrypting with the private key, or using the MD5 hashing algorithm to validate the integrity of incoming data.
Requirements:
- No background requirements
Who this course is for:
- Beginners
- Intermediate and advanced professionals
Course Rating: 4.6/5
Enroll here: https://www.udemy.com/course/cybersecurity-from-beginner-to-expert/
https://www.udemy.com/ 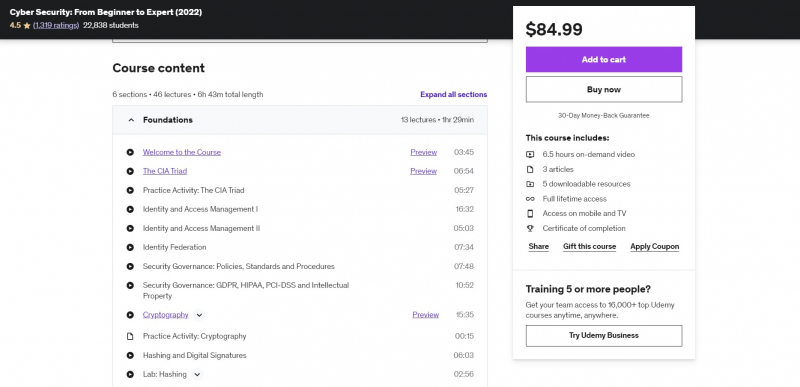
https://www.udemy.com/ -
Learn how to combat various types of online threats, such as sophisticated hackers, trackers, malware, zero-day exploits, exploit kits, cybercriminals, and more. Make a career as a cyber security expert - This easy-to-follow expert course will take you from beginner to advanced. All major systems are covered, including Windows 7, Windows 8, Windows 10, macOS, and Linux.
This course covers the essential building blocks of your necessary skill set: threat modeling and risk assessments will help you comprehend the threat and vulnerability landscape. This course delves into the Darknet and the cybercriminal's thinking. Malware, exploit kits, phishing, zero-day vulnerabilities, and a lot more are all covered. You'll learn about nation-state-run worldwide tracking and hacking infrastructures. Covering the capabilities of the NSA, FBI, CIA, GCHQ, China's MSS, and other intelligence services.
You'll learn the fundamentals of operating system security and privacy features. A look at the new privacy problems in Windows 10 and how to effectively deal with them. There's a comprehensive, easy-to-understand crash course on encryption, including how it may be circumvented and what you can do to limit the dangers. Master the art of phishing, SMShing, vishing, identity theft, scams, cons, and other forms of social engineering. Finally, it discusses the critical yet underappreciated security controls of isolation and compartmentalization.
Requirements:
- A fundamental grasp of operating systems, networks, and the Internet is required
Who this course is for:
- Beginners and intermediate Internet users
Course Rating: 4.5/5
Enroll here: https://www.udemy.com/course/the-complete-internet-security-privacy-course-volume-1/
https://www.udemy.com/ 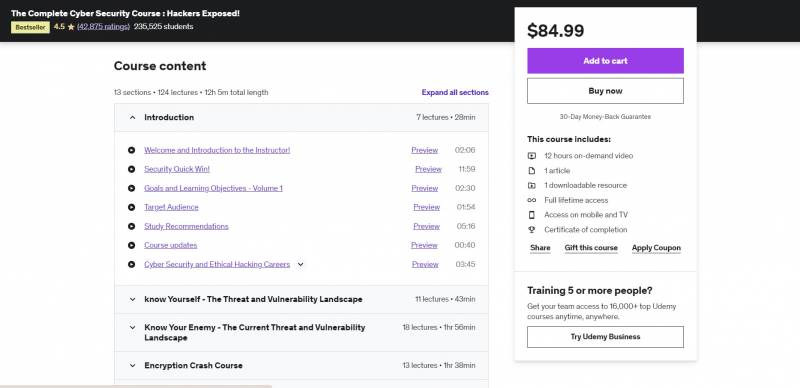
https://www.udemy.com/ -
The course will begin by teaching fundamental operations, then go on to discussing and explaining Distributed Control Systems, and finally covering SCADA. It then goes on to describe the OT Network and Purdue Reference Model, as well as other OT terms and contrasts from IT. You will have a strong grasp of OT system components and logical designs at this time. The course will next progress to advanced topics in OT protocols and communications, with a deep technical dive into industrial protocol followed by multiple laboratories, and ultimately, the teacher will discuss OT Cybersecurity Controls and Solutions in the last session.
This course will be updated on a regular basis, with new bonus and gift videos as well as some intriguing and sophisticated topics related to OT Cybersecurity. This course will teach you the fundamentals of operational technology, as well as how to comprehend the various systems within OT and how to apply your IT Cybersecurity expertise to the realm of OT.
Requirements:
- Beginners in IT Cybersecurity
Who this course is for:
- IT Cybersecurity professionals who wants to understand the fundamentals of OT
Course Rating: 4.5/5
Enroll here: https://www.udemy.com/course/fundamentals-of-ot-cybersecurity/
https://www.udemy.com/ 
https://www.udemy.com/ -
Working in a security operations center is the focus of this course (SOC). Its goal is to generate SOC analysts that are well-versed in cyber security fundamentals, technological solutions, security operations, and incident response. Learners will be ready to strike the ground running on their first day on the job after completing the course. Learners will also obtain a thorough grasp of the common tools, people, and operational processes and procedures that go into successfully delivering SOC functions. Because the door to the SOC is constantly open, SOC analysts will always be in great demand.
This course is guaranteed to provide learners with all they need to work as an entry-level SOC analyst capable of competing with intermediate analysts. This course covers technological solutions and suppliers across several cyber defense domains; as a result, learners will obtain a thorough grasp of security technologies that are often used in workplace contexts, allowing them to have relevant dialogues with future employers.
Requirements:
- Basic understanding of Information Technology concepts
Who this course is for:
- College Graduates
- IT Professionals
- Cyber Enthusiasts
- Cyber Security Internship Seekers
Course Rating: 4.4/5
Enroll here: https://www.udemy.com/course/cyber-security-operations-and-technology-solutions/
https://www.udemy.com/ 
https://www.udemy.com/ -
Did you know that almost half of all employees save company data to a personal laptop? Is there anything you can do in this situation? Yes, set up a Data Loss Prevention (DLP) system for Windows, Mac OS X, Linux, and mobile devices to prevent data loss or theft. Protect your important data, client details, credit card numbers, and other personal information. You control when, where, and by whom data may be read and copied using a DLP system!
This is a vendor-neutral introduction course that covers DLP systems, architecture, components, and features at a high level. There are hands-on labs involved! This is a vendor-neutral training that will prepare you to use any DLP system, including business Symantec or McAfee systems. Device Lock and Endpoint Protector are the two DLP systems used in the hands-on labs. This is a practical course. Join today to learn more about what a DLP system can accomplish for you and your business!
Requirements:
- IT security principles should be understood at a basic level
- Understanding of the fundamentals of networking
- Understanding of virtualization and servers at a basic level
Who this course is for:
- Engineers and managers
- Beginners
Course Rating: 4.2/5
Enroll here: https://www.udemy.com/course/data-loss-prevention-dlp-security-breaches-under-control/
https://www.udemy.com/ 
https://www.udemy.com/